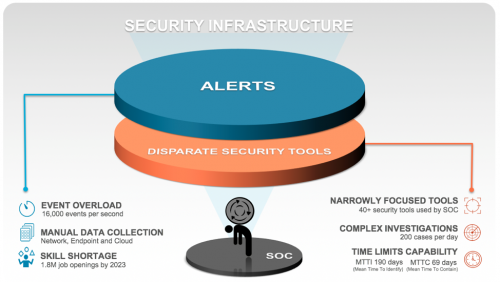
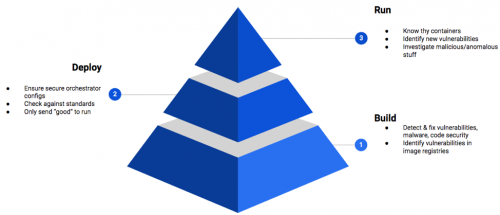
For many organizations, security teams are the first line of defense against all known and unknown threats. The core function of these teams is to identify, investigate and mitigate threats across their entire digital domain. As adversaries become more automated and complex, security teams are relying on a layered approach to prevention. This approach involves
2019 May
- 02
May - 0
- 1:57am
Runc and CVE- 2019-5736: A Container Security Triad Love Story
If you’ve been putting off addressing container security, today might be the day to make it a priority. In the last 24 hours, a critical vulnerability was reported that affects runc. Don’t be surprised if you’ve never heard of it. It’s the runtime that supports Docker, Kubernetes (k8s) and many other related services. While the
- 02
May - 0
- 1:57am
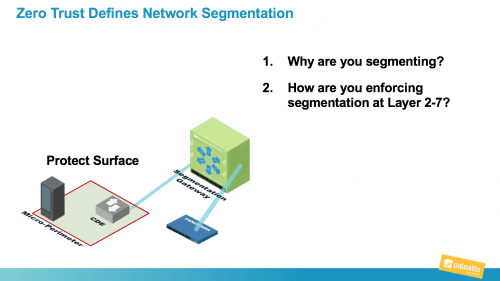
You Want Network Segmentation, But You Need Zero Trust
In this blog series, I’ve been giving sufficient commentary on Zero Trust in order to dispel much of the mythology that has started to surround the topic recently. I talked about the fundamental issues with the failed trust model and how trust is a vulnerability. Then, I provided clarity as to what Zero Trust is
- 02
May - 0
- 1:57am
When Scripts Attack, WildFire Protects
Adversaries look for fast and easy ways to steal data. Among the many techniques in their playbooks, using scripts is a quickly growing trend. Why? It requires minimum human intervention, automates manual steps, and gets them to their malicious goals faster. Scripting is an extremely useful tool. It allows administrators and power-users to automate repetitive
- 02
May - 0
- 1:57am
Build Confidence in Your Security Controls with a Self-Service Best Practice Assessment
Over the past several months, customers have been asking for the ability to run a Best Practice Assessment (BPA) more frequently, on their schedule, and in their own environment. We are happy to share that we have been able to do all of this without sacrificing any of the features that customers love. On November
- 02
May - 0
- 1:57am
Machine Learning: Your Unfair Advantage Against Attackers
In the never-ending arms race between threat actors and defenders, automation and machine learning have become your ultimate weapons. Today, threat actors employ automation in countless ways to speed up their attacks and evade detection. Outpacing attackers requires the effective use of automation and machine learning. Years ago, our research and development teams recognized it
- 02
May - 0
- 1:57am
Cybersecurity Canon Candidate Book Review: “Abundance: The Future Is Better Than You Think
We modeled the Cybersecurity Canon after the Baseball or Rock & Roll Hall-of-Fame, except for cybersecurity books. We have more than 25 books on the initial candidate list, but we are soliciting help from the cybersecurity community to increase the number to be much more than that. Please write a review and nominate your favorite. The Cybersecurity Canon
- 02
May - 0
- 1:57am
Get Your Copy of the Cybersecurity Career Guide: Who Works in Cybersecurity, How We Got Started, Why We Need You
Cybersecurity needs you. Beginning a new career path in cybersecurity can be daunting, especially if you don’t know what to do, who to talk to, and whether you’re even ready to get started. The goal for this book is to provide the information you need to kick-start your career in cybersecurity. We reached out to
- 02
May - 0
- 1:57am
Understanding Illicit Cryptocurrency Mining: Threats and Best Practices for Prevention
Anything that has significant monetary value eventually attracts criminal activity. Such is the case with cryptocurrency, which since its earliest days has played a role in everything from the online purchases of illegal items to ransom demands from the bad actors behind ransomware attacks. More recently we’ve witnessed the rise of illicit cryptocurrency mining, also
- 01
May - 0
- 1:00pm
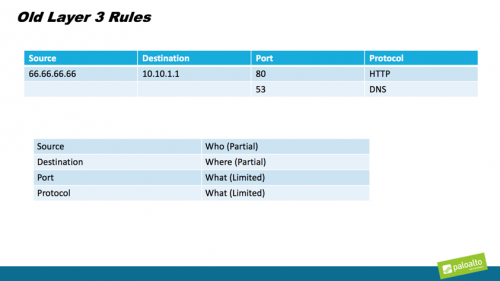
All Layers Are Not Created Equal
How the Principles of Journalism Help Define Zero Trust Policy Everyone knows that in order for a news article, blog post or white paper to have any credibility, a writer needs to cover the “who, what, where, when, why and how” of the topic. Without covering these things, the reader is left with a