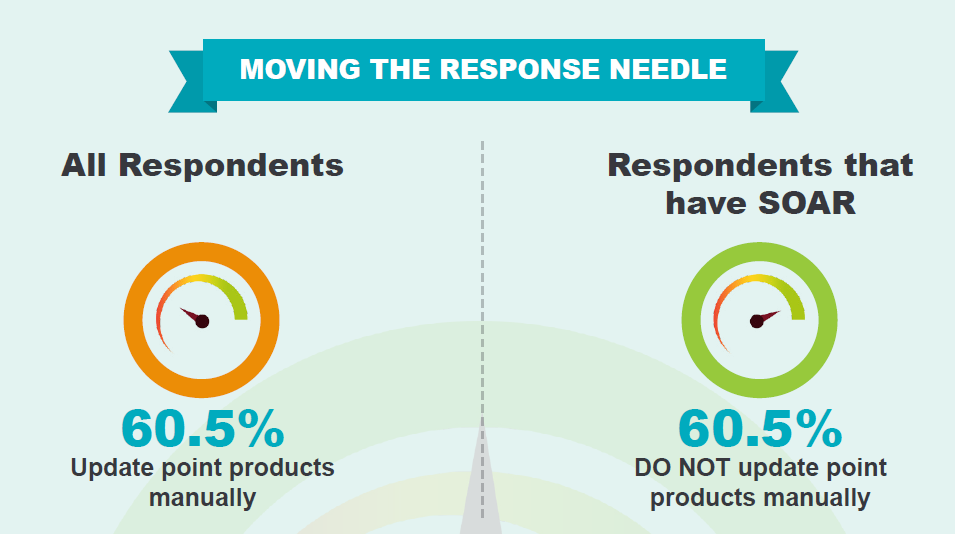
This piece was originally published August 7 on the Demisto blog. For the third annual report on the state of SOAR (Security Orchestration, Automation and Response), we at Demisto commissioned a study with 552 security practitioners. Our aim was to find out specific challenges at each stage of the incident response lifecycle, how current product
2019 August
- 12
Aug - 0
- 4:00pm
XDR Gains Traction as Customers, Analysts, Vendors Embrace New Category
Palo Alto Networks founder Nir Zuk last year called for radically transforming the security market by creating a new product category for endpoint protection: XDR. We launched the category in February with the release of Cortex XDR and other players have announced their intent to enter the XDR market soon. XDR is the next leap
- 09
Aug - 0
- 12:03pm
Kubernetes Penetration Test Report: Insights and Twistlock Response
The Cloud Native Computing Foundation (CNCF) late last year commissioned a penetration test to identify unknown security vulnerabilities and design weaknesses in Kubernetes. The final report is posted in the working group’s repository. When done well, penetration tests provide methods for improving software security quality. The Kubernetes test was thorough and well designed. It resulted
- 09
Aug - 0
- 12:03pm
From ‘DevOps vs. SecOps’ to DevSecOps
DHI Group runs 100% in AWS. We provide a job recruiting platform for technical candidates and businesses in the United States as well as Europe and Asia-Pacific. AWS helps us deliver features to customers more quickly and reduce data center costs. When I joined the company about two years ago, we were at the end
- 07
Aug - 0
- 10:00pm
NSS Labs 2019 BPS Test: Palo Alto Networks Earns ‘Recommended’ Rating
Palo Alto Networks achieved a “Recommended” rating in the 2019 NSS Labs Breach Prevention Systems (BPS) test, the highest rating NSS Labs offers. The test included our Next-Generation Firewall with Threat Prevention, WildFire malware analysis service, and Traps endpoint protection and response. By natively integrating advanced threat intelligence into network, cloud and endpoint security, we
- 06
Aug - 0
- 12:00pm
8 Tips for Surviving Black Hat and Other Hostile Networks
For the third year in a row, Palo Alto Networks will collaborate with other top security vendors and experts who help run the Black Hat Network Operations Center (NOC). We help provide stability, visibility and security in the NOC. If you’re heading to Las Vegas this week for Black Hat, BSides or DEF CON, you should
- 05
Aug - 0
- 10:18am
SEGA Europe: You Cannot Protect What You Cannot See
As a prolific game developer and publisher with six studios across four countries, SEGA Europe needed greater visibility into vulnerabilities existing across its network and more granular control over application traffic to mitigate exposure to malware and other cyber exploits. This article describes how Palo Alto Networks Security Operating Platform helps SEGA Europe serve its
- 05
Aug - 0
- 10:18am
Change Healthcare’s Road to Cloud Compliance is Paved with Lessons Learned
Traditionally, Change Healthcare operated in a legacy data center environment. That is until about 5 years ago when we set out on our digital transformation journey with all roads leading to the cloud. Fast forward to today, the cloud provides us with a common architecture that our business relies on to support operations across our
- 05
Aug - 0
- 10:18am
Advantages of Cloud-Delivered Security for U.S. Govt Agencies
Last year, three-quarters of the U.S. federal government’s IT budget were spent on supporting and maintaining legacy systems. Combined with the Cloud Smart strategy, agencies have more reasons than ever to consider cloud alternatives to on-premise applications, services and storage. Cybersecurity is one cloud service that can make a big impact. Like other services from
- 05
Aug - 0
- 10:18am
Two Weapons to Help U.S. Govt Combat Cyberthreats
Federal agencies face a conundrum: They are the targets of relentless cyberattacks yet lack enough skilled personnel to combat them. State-affiliated actors, responsible for more than half of public administration data breaches1 combine never-before-seen malware with other techniques to infiltrate agencies and steal data or disrupt operations. With many thousands of new threats created every day,2