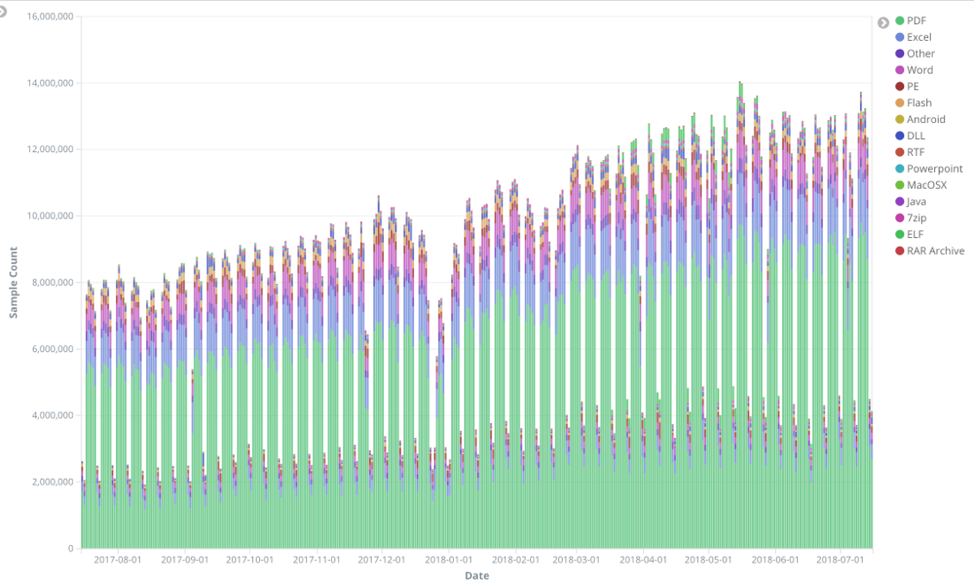
Over the past several months, customers have been asking for the ability to run a Best Practice Assessment (BPA) more frequently, on their schedule, and in their own environment. We are happy to share that we have been able to do all of this without sacrificing any of the features that customers love. On November
admin
- 26
Oct - 0
- 8:00pm
Machine Learning: Your Unfair Advantage Against Attackers
In the never-ending arms race between threat actors and defenders, automation and machine learning have become your ultimate weapons. Today, threat actors employ automation in countless ways to speed up their attacks and evade detection. Outpacing attackers requires the effective use of automation and machine learning. Years ago, our research and development teams recognized it
- 26
Sep - 0
- 12:00pm
Cybersecurity Canon Candidate Book Review: “Abundance: The Future Is Better Than You Think
We modeled the Cybersecurity Canon after the Baseball or Rock & Roll Hall-of-Fame, except for cybersecurity books. We have more than 25 books on the initial candidate list, but we are soliciting help from the cybersecurity community to increase the number to be much more than that. Please write a review and nominate your favorite. The Cybersecurity Canon
- 25
Sep - 0
- 12:00pm
Get Your Copy of the Cybersecurity Career Guide: Who Works in Cybersecurity, How We Got Started, Why We Need You
Cybersecurity needs you. Beginning a new career path in cybersecurity can be daunting, especially if you don’t know what to do, who to talk to, and whether you’re even ready to get started. The goal for this book is to provide the information you need to kick-start your career in cybersecurity. We reached out to
- 19
Sep - 0
- 1:15pm
Understanding Illicit Cryptocurrency Mining: Threats and Best Practices for Prevention
Anything that has significant monetary value eventually attracts criminal activity. Such is the case with cryptocurrency, which since its earliest days has played a role in everything from the online purchases of illegal items to ransom demands from the bad actors behind ransomware attacks. More recently we’ve witnessed the rise of illicit cryptocurrency mining, also
- 04
Sep - 0
- 5:00pm
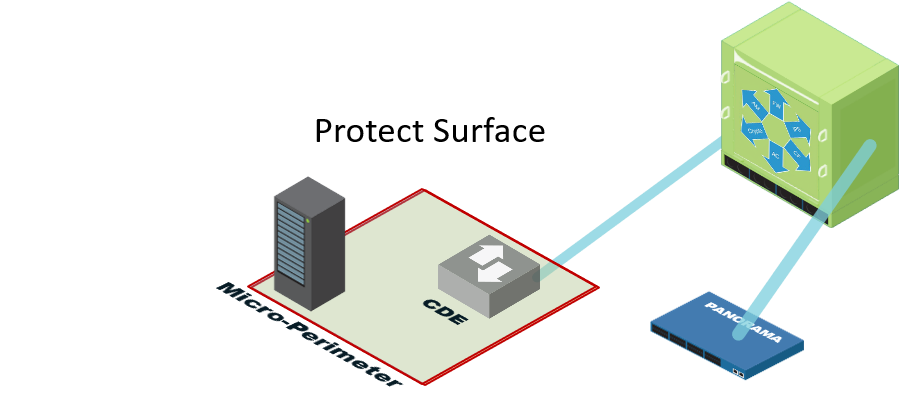
Define a Protect Surface to Massively Reduce Your Attack Surface
In cybersecurity, one of the things people tend to focus on the least is defining what they’re trying to protect. The general consensus is that they want to protect against attacks, but the attacks are attacking something. What is that thing? Over the years, we have been working diligently to reduce the attack surface, but