Here at Aruba we are focused on hearing the voice of the customer to improve customer experience at each interaction with Aruba; whether it is here on the web, when you call, interact with our sales force, etc. As part of our ongoing effort to listen more to customers we are reaching out for your
admin
- 14
Apr - 0
- 8:57pm
Give a kudos and help bring a Lithy home! Voting extended until August 31, 2018 at 5:00 pm PT!
We had fun creating our Airheads community campaign for EMEA Atmosphere that we decided to submit the Security Survey as part of the upcoming Lithium 2018 Lithy awards. The campaign would not have been such a success without the Airheads support and participation. So, give a kudos and help bring a Lithy home! We
- 14
Apr - 0
- 8:57pm
Atmosphere Meetup Topic Selection, Vote Now!
Hello Airheads! Back by popular demand we are taking the best of Atmosphere 2018 on the road! However, we heard your feedback from last year and want to bring the technical depth you are looking for. Please take 2 minutes to provide your feedback so we can try to customize the content to your
- 14
Apr - 0
- 8:57pm
Meet the Insiders: John Welsh
I sat down with John Welsh, a solutions architect and pre-sales engineer, to get the skinny on what he does, what he’s looking forward to at the conference, and the future of technology. Follow John on Twitter at @SampleFive. Don’t miss his blog www.samplefive.com. PK: When you’re not hanging out at ATM18, what’s
- 14
Apr - 0
- 8:57pm
Meet the Insiders: Jonathan Davis
I had an opportunity to sit down with one of our ATM Insiders, Jonathan Davis, to get the inside scoop on what he does, what he’s looking forward to at the conference and the future of technology. Be sure to follow Jonathan on Twitter at @Subnetwork and check out his “It must be the network…”
- 14
Apr - 0
- 8:57pm
Meet the Insiders: Jake Snyder
I sat down with Jake Snyder, a distinguished system engineer at CompuNet, to get the skinny on what he does, what he’s looking forward to at the conference and the future of technology. Follow Jake on Twitter at @JSnyder81. Don’t miss his brand-new blog ToDSfromDS and his YouTube channel. PK: When you’re not
- 20
Feb - 0
- 2:00pm
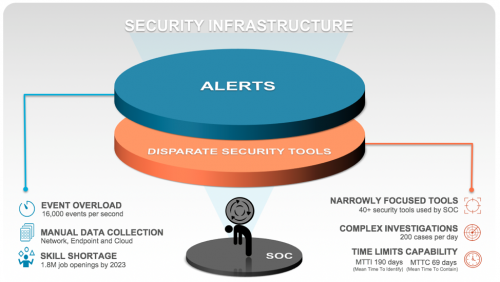
Security Teams Deserve a Better Approach to Detection and Response
For many organizations, security teams are the first line of defense against all known and unknown threats. The core function of these teams is to identify, investigate and mitigate threats across their entire digital domain. As adversaries become more automated and complex, security teams are relying on a layered approach to prevention. This approach involves
- 12
Feb - 0
- 6:48pm
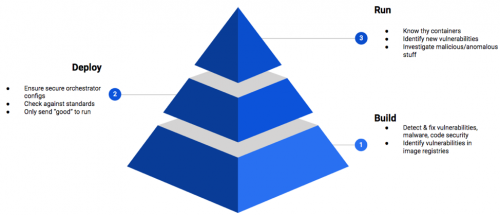
Runc and CVE- 2019-5736: A Container Security Triad Love Story
If you’ve been putting off addressing container security, today might be the day to make it a priority. In the last 24 hours, a critical vulnerability was reported that affects runc. Don’t be surprised if you’ve never heard of it. It’s the runtime that supports Docker, Kubernetes (k8s) and many other related services. While the
- 17
Jan - 0
- 2:00pm
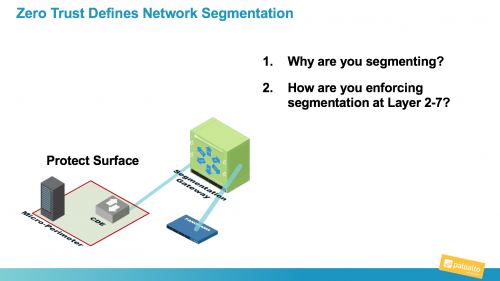
You Want Network Segmentation, But You Need Zero Trust
In this blog series, I’ve been giving sufficient commentary on Zero Trust in order to dispel much of the mythology that has started to surround the topic recently. I talked about the fundamental issues with the failed trust model and how trust is a vulnerability. Then, I provided clarity as to what Zero Trust is
- 16
Jan - 0
- 2:00pm
When Scripts Attack, WildFire Protects
Adversaries look for fast and easy ways to steal data. Among the many techniques in their playbooks, using scripts is a quickly growing trend. Why? It requires minimum human intervention, automates manual steps, and gets them to their malicious goals faster. Scripting is an extremely useful tool. It allows administrators and power-users to automate repetitive