Lindsey Sanford is the Global Employer Brand Program Manager at Palo Alto Networks. She lives in Reno, Nevada, and has been a Girl Scout Troop leader for two years. Her Girl Scouts have earned all three Daisy cybersecurity badges, and are pursuing badges in engineering and programming. In the mid-60s to late 70s, 4,807
admin
- 05
Aug - 0
- 10:18am
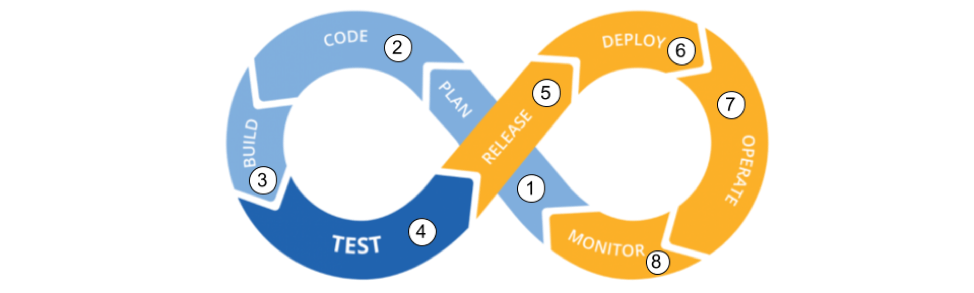
4 Practical Steps for ‘Shift Left’ Security
Since the beginning of modern computing, security has largely been divorced from software development. Recent vulnerability research confirms this. Consider that over the past five years, out of all published vulnerabilities, 76% were from applications. Given this radical shift in attacker focus, it’s time to embed security with development. The best way to get this
- 05
Aug - 0
- 10:18am
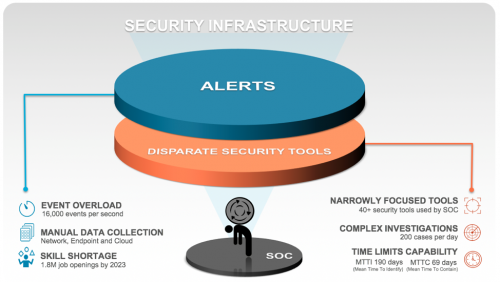
How to Help SOC Analysts Fight ‘Alert Fatigue’
Palo Alto Networks survey data shows that SOC analysts are only able to handle 14% of alerts generated by security tools. When you consider IDC data showing that most alerts are false positives,[1] the results are predictable: Alerts get ignored, analysts waste time chasing false leads, and actual threats get missed. Beyond initial prevention, most
- 05
Aug - 0
- 10:18am
Seven Guiding Principles to Selecting the Right Cloud Security Solution
Allan Kristensen, Sr. Director, Systems Engineering, Public Cloud at Palo Alto Networks. I recently had the opportunity to chat with Palo Alto Networks Senior Director of Worldwide Public Cloud Security SEs, Allan Kristensen, who brings 15+ years of experience building highly effective solutions engineering (SE) teams. The Palo Alto Networks SE team has firsthand knowledge
- 05
Aug - 0
- 10:18am
NSS Labs 2019 NGFW Group Test: Highest Security Effectiveness Score
We are excited to announce that Palo Alto Networks has achieved the highest Security Effectiveness score among all twelve products included in this year’s NSS Labs NGFW group test. Our NGFW blocked 100% of evasions, and it earned a “Recommended” rating. Highlights from our test results include: Highest Security Effectiveness score 100% evasions blocked (406
- 05
Aug - 0
- 10:18am
How Western Asset Management Is Mitigating Cloud Threats
Banking, investment management and FinTech have continually invested in technology upgrades, data analytics and differentiated product offerings in an increasingly competitive and evolving investment landscape. A recent Accenture survey found 90% of banking respondents stating that cloud enables and accelerates innovative adoption. Of those surveyed, 60% say cloud-based entrants will challenge traditional businesses shackled by
- 02
May - 0
- 1:57am
Security Teams Deserve a Better Approach to Detection and Response
For many organizations, security teams are the first line of defense against all known and unknown threats. The core function of these teams is to identify, investigate and mitigate threats across their entire digital domain. As adversaries become more automated and complex, security teams are relying on a layered approach to prevention. This approach involves
- 02
May - 0
- 1:57am
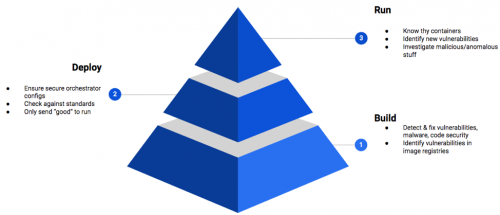
Runc and CVE- 2019-5736: A Container Security Triad Love Story
If you’ve been putting off addressing container security, today might be the day to make it a priority. In the last 24 hours, a critical vulnerability was reported that affects runc. Don’t be surprised if you’ve never heard of it. It’s the runtime that supports Docker, Kubernetes (k8s) and many other related services. While the
- 02
May - 0
- 1:57am
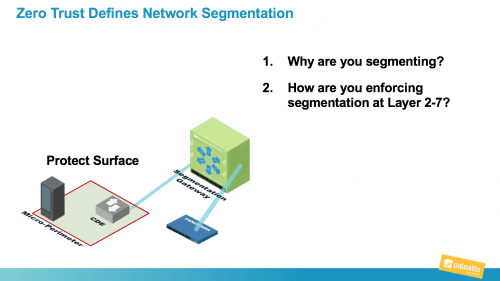
You Want Network Segmentation, But You Need Zero Trust
In this blog series, I’ve been giving sufficient commentary on Zero Trust in order to dispel much of the mythology that has started to surround the topic recently. I talked about the fundamental issues with the failed trust model and how trust is a vulnerability. Then, I provided clarity as to what Zero Trust is
- 02
May - 0
- 1:57am
When Scripts Attack, WildFire Protects
Adversaries look for fast and easy ways to steal data. Among the many techniques in their playbooks, using scripts is a quickly growing trend. Why? It requires minimum human intervention, automates manual steps, and gets them to their malicious goals faster. Scripting is an extremely useful tool. It allows administrators and power-users to automate repetitive